Service

- Service
-
Security Consulting
(Penetration Testing)
Notice: Undefined offset: 3 in /home/host/stealien/www/html/_skin/layout/inc_navigation_middle.php on line 86
Home > Service > Penetration Testing
Security Consulting
(Penetration Testing)
We analyze vulnerabilities in various service environments such as web, mobile, IoT, cloud services, and other new technologies. Based on these, we create a feasible threat scenario and suggest appropriate countermeasures and improvements.
Advanced Hacking Service

- World-class Hackers
-
- Awards from global hacking contests such as CODEGATE, HITB CTF, DEFCON, etc.
- Lots of the best awards from the vulnerability reward system by KISA.
- Vulnerabilities discovery of global vendor companies such as Windows Kernel, Google Chrome, Adobe, and VMware.

- Security consulting in attacker’s perspective
-
- Penetration testing provided by white hackers, in attacker’s perspective.
- Critical vulnerabilities discovered through black-box testing.

- Rich experience & high-level techniques in diagnosing vulnerabilities
-
- Various experiences in web, mobile, IoT, intranet, APT, etc.
- Many successful security consultations of finance, large corporations, public institutions, etc.
Examples of Penetration Testing
-
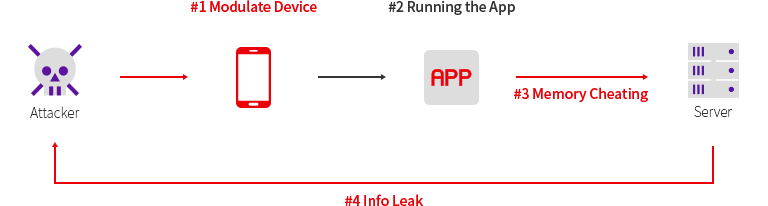
1. Hacking critical information through device modulation
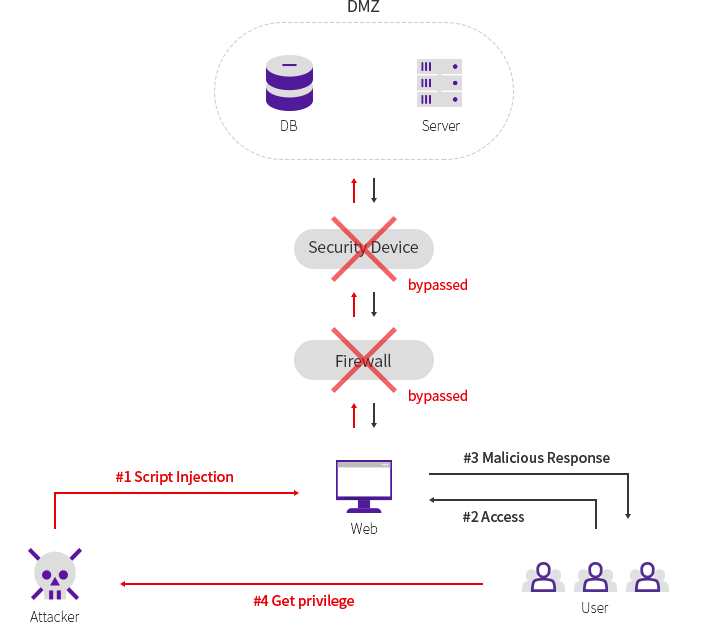
2. Hacking critical information and taking control of the server
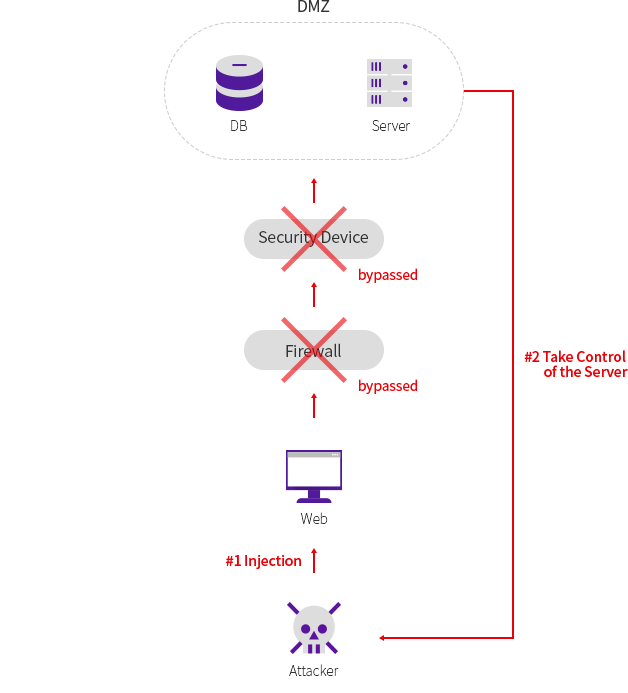
-
1. Hacking critical information through device modulation
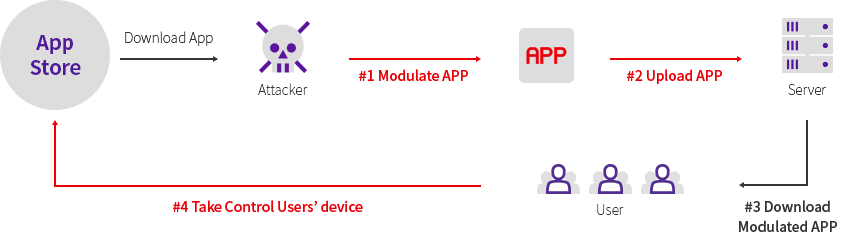
2. Taking control of the device through app modulation